
How to Minimize Network Downtime and Increase Efficiency
With so many business activities occurring online, downtime can be disastrous for modern organizations — and its frequency and financial effects are only increasing. In the Uptime Institute’s 2022 report, over 60% of outages cost at least $100,000 in total losses, and almost a third lasted over 24 hours. Both values reflect substantial increases from prior years.
Unfortunately, many sources can cause downtime. Pinpointing the issue may not be straightforward, leading to time-consuming fixes. We’ve outlined some strategies for reducing unplanned downtime to help you keep your business moving and limit the effects of outages.
Downtime Reduction Strategies
Prevention is the best way to limit downtime. Whether you currently face issues with downtime or want to stay prepared, try these tactics to avoid problems.
1. Audit and Monitor Your Entire System
Start by thoroughly analyzing your entire system, including internal and external risks. During this process, you’ll identify weak points that can tell you where to focus your efforts. Look for potential issues by reviewing every asset, including:
- Routers
- Servers and software
- Power supplies
- Cables
- Cloud service providers
- Internet service providers
- Utility providers
Document any possible vulnerabilities. If a network outage occurs, you can check these vulnerabilities first to minimize the length of downtime. With the complete picture of your IT infrastructure, you can implement constant monitoring for each network component. Real-time monitoring solutions allow you to respond faster, preventing downtime and minimizing the workload.
2. Build Redundancy
With a redundant network connection, you can seamlessly switch from one ISP to another if your primary provider goes down. Redundant systems help reduce the damaging effects of errors or shutdowns and ensure continued operations. If you have speed issues, a redundant network might also offer more paths for accessing data, allowing you to use the fastest one at a given time.
Data redundancy is valuable, too. Storing your information in a secondary location with backup services can ensure access to critical resources even if your primary data storage site goes offline.
3. Implement Backup Power
Another type of redundancy is backup power. An uninterruptible power supply detects when the primary power source fails, powering up immediately to keep your electronics online. These devices typically provide power for about 30 to 60 minutes — plenty of time to save work and safely shut down electronics. This time frame is also enough to support tasks like making sales or accessing information during brief periods of power interruption.
A UPS handles power conversions for highly sensitive technology, so you should include it in your maintenance and testing plans.
4. Create a Robust Maintenance Strategy
Maintenance is crucial for any IT infrastructure. From routine firmware and software updates to equipment configurations and testing, robust maintenance supports your devices’ ongoing performance. Ensure your plan includes preventive maintenance, which involves identifying and fixing problems before they cause unplanned downtime.
5. Invest in Quality Equipment
Always select your IT equipment for the job at hand and invest in high-quality systems. While quality hardware might cost more upfront, reliable performance and reduced downtime can save you significantly in the future.
Solutions to Common Networking Problems
The Uptime Institute report found networking issues to be the top cause of IT service downtime incidents. Even if it doesn’t cause a complete outage, a slow network can adversely impact your efficiency, limiting your ability to conduct day-to-day operations. If you frequently experience lagging apps, slow Internet speed, interrupted voice calls and other connection problems, assessing your network could help you improve operational efficiency.
Network downtime can happen due to these internal and external factors.
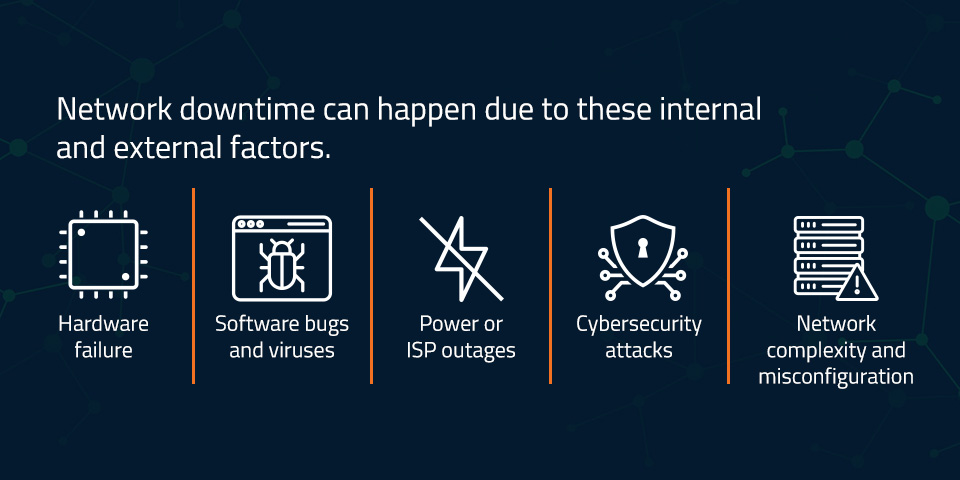
- Hardware failure: Many types of hardware can fail due to age, damage and overheating. Even something as innocuous as a cable chewed up by a mouse can lead to costly network outages. Some networking devices that deserve special attention include firewalls, routers, switches and network interface cards. Regularly evaluate your hardware assets’ condition and capabilities.
- Software bugs and viruses: Software issues can cause network problems, too. Perform firmware and software updates as needed, and regularly evaluate your software solutions to keep these issues at bay.
- Power or ISP outages: Utility providers and ISPs often have outages due to inclement weather conditions like high winds or blizzards. Other reasons you might have an outage include wildfires and damage to infrastructure, like a downed power line from a fallen tree. Redundant networks and power backups can mitigate these unpredictable circumstances.
- Cybersecurity attacks: Cybersecurity attacks like denial of service and spoofing can target your network. You can better resist cybersecurity threats by following comprehensive security practices, including network monitoring.
- Network complexity and misconfiguration: Highly complex networks often create opportunities for human error and misconfiguration. You can minimize risk with straightforward IT infrastructure, transparent workflows and a knowledgeable team.
Continuous monitoring is one of the best ways to prevent network downtime and boost efficiency. Once in place, it can help you determine which devices cause problems under what scenarios. Effective monitoring software can reduce your team’s workload and minimize human error. Since networking issues have many potential sources, monitoring allows you to respond flexibly to different scenarios.
Apply thorough network monitoring at strategic points throughout your network, such as routers, switches and user devices. Developing a remote monitoring solution can help you build an at-a-glance view of how data flows across the network. It delivers real-time information for quickly pinpointing problem areas and preventing or shortening outages. Monitoring can also offer insights into long-term needs, such as future upgrades or changes in capacity.
As you monitor the network, collect data on its behavior to establish baselines. For example, you might gather information on bandwidth and latency during typical usage conditions. Once you know how your network usually behaves, you can determine thresholds and set up alerts for out-of-range situations. Investigating alerts also becomes simpler, as you can quickly analyze traffic routes to optimize performance.
Maximize Uptime With Morefield
When power or networking issues affect a business, they can bring operations to a halt and significantly increase costs. They can even put your reputation or compliance at risk. Tackling downtime calls for a comprehensive approach and knowledgeable IT professionals. If you do business in Pennsylvania, work with the experts at Morefield.
We offer a wide range of services, including managed IT services that allow our experienced team to handle time-consuming tasks like maintenance, backups and tech support. We can also offer support in specific areas like cybersecurity and wireless networking. Reach out today to discuss how we can optimize your uptime.






